Insider Threat Detection with SOFIT
Introduction
Organizations understand the dangers that outside threats, such as hackers or unethical competitors, can pose to their operations. Insider threats, however, are less widely understood – but no less dangerous.
To fill the gaps among current security approaches, Dr. Frank Greitzer, Justin Purl, Yung Mei Leong, and D.E. (Sunny) Becker have proposed a powerful new approach, called SOFIT (Sociotechnical and Organizational Factors for Insider Threat).
Cogynt lets organizations implement SOFIT more quickly, easily, and effectively than any other commercially available solution. In this sample project, we have created an introductory model to showcase how Cogynt leverages SOFIT to predict and prevent insider threats before they can do serious damage.
Thanks to Cogynt's flexibility of application and robust modeling capabilities, you can adapt and refine this introductory model's approach to suit your organization's needs.
To request a copy of the SOFIT model, please contact Cogility.
Understanding SOFIT
Originally designed and implemented as an ontology using Web Ontology Language (OWL), SOFIT has evolved into the most extensive knowledge base of individual factors (both behavioral/psychosocial and technical/cyber) available in open literature. SOFIT is unique in that it specifies the applicable organizational factors associated with insider threats. SOFIT was the most comprehensive base of factors at the time of its release, and remains the most comprehensive to date.
SOFIT considers a wide array of individual and organizational factors associated with the risk of insider threats:
- Individual factors encompass behaviors, attitudes, personal issues, sociocultural or ideological factors, and various biographical factors that may indicate an elevated risk.
- Organizational factors pertain to management practices, policies, the work environment, workload, and other workplace aspects that can contribute to performance deficiencies and human error, playing a significant role in unintentional insider threats.
The SOFIT knowledge base includes over 300 constructs or factors focusing on individual characteristics or behaviors. An additional 50 or so factors address organizational vulnerabilities. These individual and organizational factors can be indicative of a number of insider threats, including:
- Espionage
- Sabotage
- Embezzlement
- Extortion
- Bribery
- Corruption
- Intellectual property theft
- Negligent use of classified data
- Fraud
- Unauthorized access to sensitive information
- Providing sensitive information to unauthorized recipients
- Workplace violence
- Unintentional insider threats
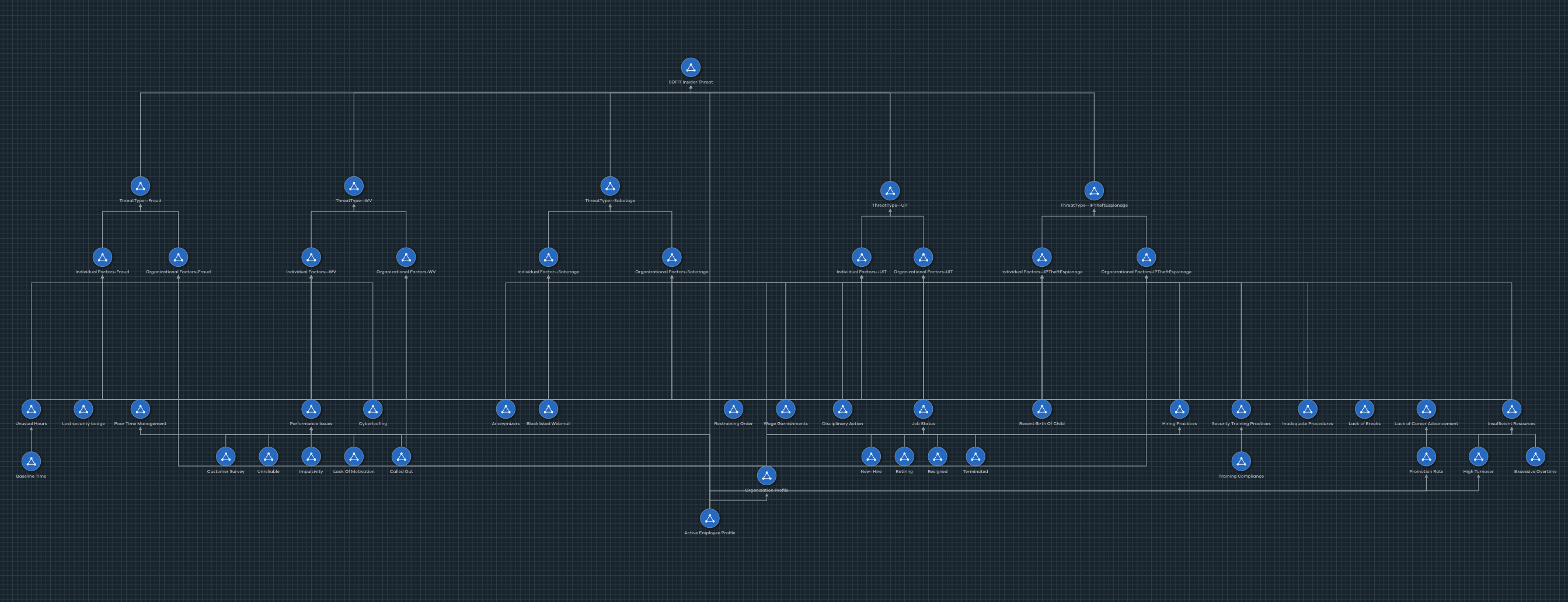
SOFIT Insider Threat Detection Hierarchy
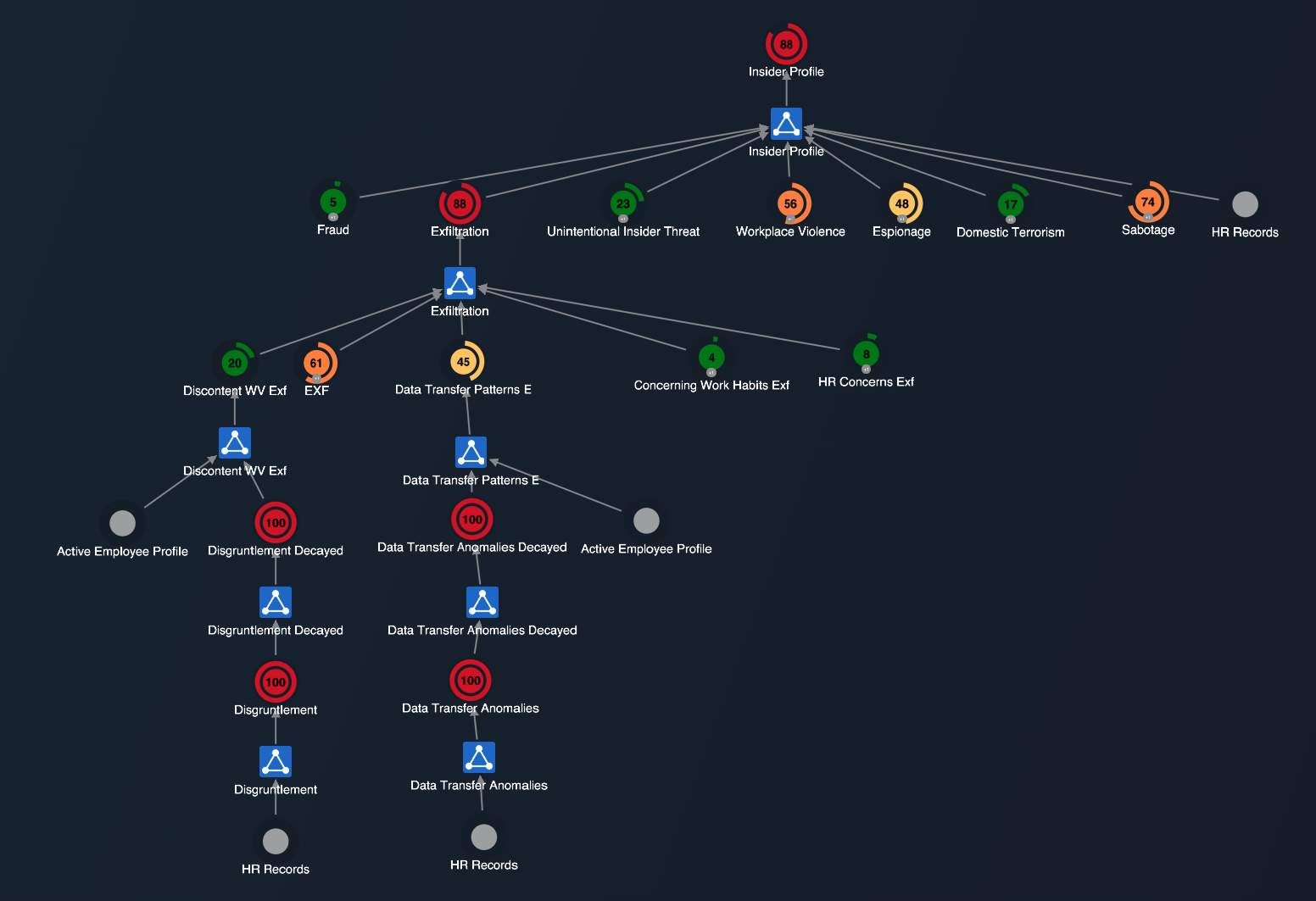
Cogynt's SOFIT model operates in a hierarchical structure with multiple layers:
- Indicator Identification: In the first layer, the model identifies various indicators, including individual and organizational factors, based on the comprehensive SOFIT model. These indicators cover a wide range of behaviors, activities, and characteristics associated with potential insider threats.
- Threat Type Assessment: In the second layer, each threat type (Fraud, Sabotage, Espionage, Data Exfiltration, Unintentional Insider Threat, and Workplace Violence) is considered. The model combines specific individual and organizational factors associated with each threat type and assigns appropriate risk scores. This step involves a thorough evaluation of the identified indicators to determine the risk level for each threat type.
- Insider Profiling: At the final level of the hierarchy, the model brings together all the threat types and assigns weights to them. These weighted threat types are then partitioned by employee number, allowing for the identification of employees posing insider threats. The model identifies the dominant threat type for each employee and provides a comprehensive profile outlining all triggered indicators associated with the specific employee.
This hierarchical structure enables a detailed analysis, starting from the identification of indicators, progressing to threat type assessment, and culminating in the detailed profiling of employees posing insider threats.
Indicator Identification Threat Factors
In this section, we outline some of the indicators used in the model, their respective data sources, and the methods used for identifying them.
We chose a limited set of individual and organizational factors here, because this project is meant to showcase Cogynt's modeling capabilities rather than offer a comprehensive threat detection solution. This model, though thorough, contains fewer than 1/3 of the factors in the full SOFIT ontology.
For a more comprehensive SOFIT model, contact Cogility.
The model assumes that organizations have access to the following data sources:
- User Activity Monitoring (UAM)
- Payroll records
- HR records (including background check reports and performance management records)
Individual Factors
Our model analyzes many individual factors, called Potential Risk Indicators (PRIs), in computing insider risk. Here we briefly describe a small, representative sample of SOFIT PRIs and how they are identified in our Cogynt model.
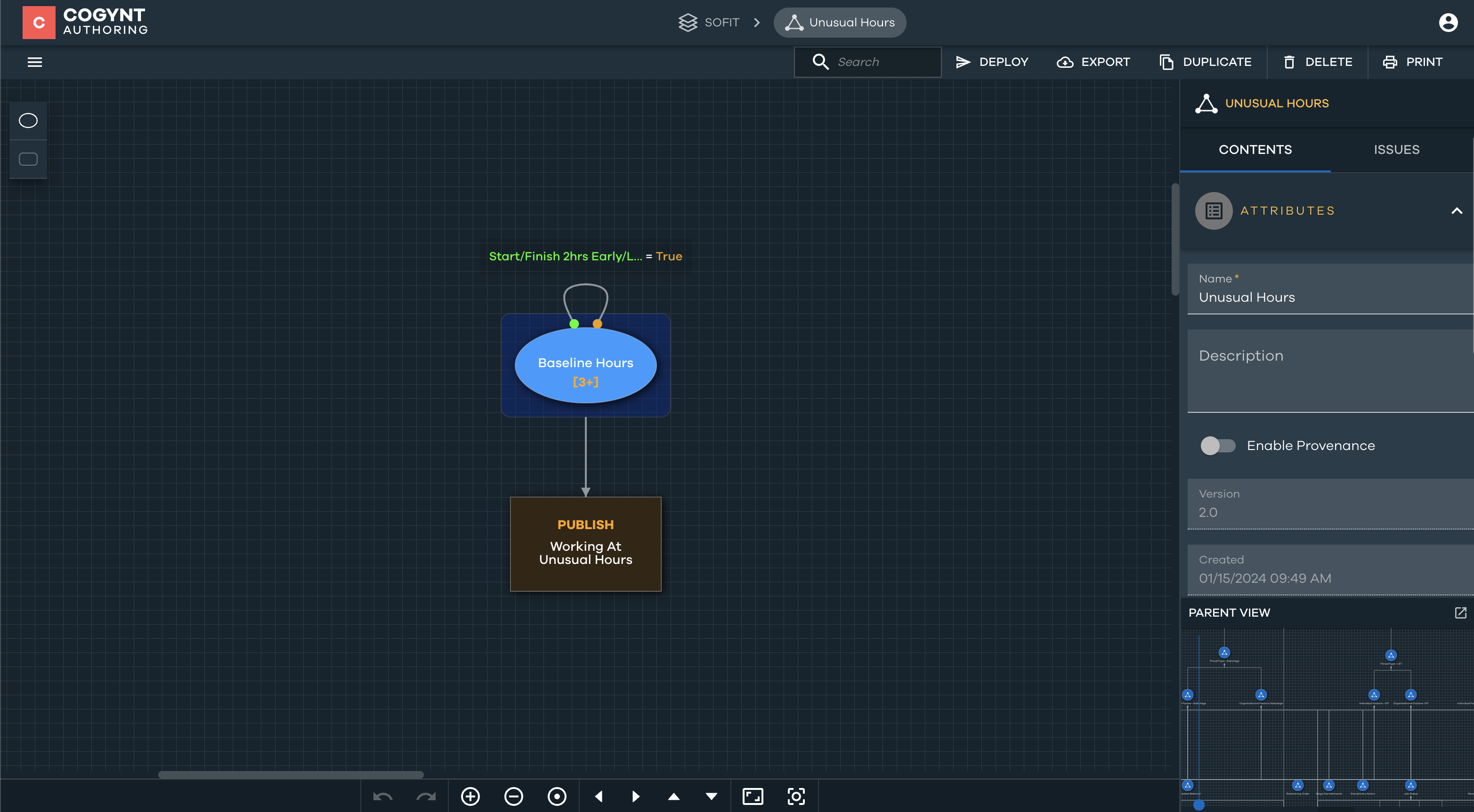
Unusual Working Hours
To determine unusual working hours, we initiate the process by establishing a baseline time for each employee. This baseline is calculated from the average time an individual accesses and exits the system, obtained from UAM records. Once this baseline is established, our criterion defines anyone starting or concluding work two hours before or after their average start or finish time, respectively, as working during unusual hours.
In this sample model, this two-hour threshold is hardcoded. However, Cogynt can employ standard deviation for a more detailed identification of individuals working at unconventional times.
Lost Security Badge
The information for lost security badges is extracted from HR records. To pinpoint instances of lost security badges, we employ lexicons to filter HR records based on the issuance reason for a security badge (such as damaged, lost, or new hire).
In this context, we focus on cases where a new badge was issued due to the loss of the previous one.
Performance Issues
Performance assessment involves analyzing five intricate patterns:
- Customer Survey: Extracted from the performance management section of HR records, this pattern filters employees based on customer survey scores. Those scoring below a predetermined minimum threshold (in our case, 4.5 out of a 5- point scale) are identified.
- Unreliable and Impulsivity: Determined through lexicons applied to manager reviews or comments in employee records. Reliablility and impulsivity patterns are recognized by analyzing the language used by managers to describe employees.
- Lack of Motivation: Based on comments from both employees and managers within the performance management section of HR reports. The lack of motivation pattern is identified by analyzing the language used in these comments.
- Called Out: Derived from payroll records, this pattern flags employees who have called out from work three or more times within a single month.
These conditions represent nominal values, and the specific criteria may vary across organizations.
Once the determination of these five conditions is completed, the Performance Issues pattern is established by considering different combinations of these factors. Each combination is then assigned a risk score, contributing to a comprehensive evaluation of an employee's performance.
![]()
Poor Time Management
The identification of poor time management is contingent on two conditions, and the presence of either signifies this pattern:
- Project Completion Past Due Date: Extracted from the performance management section of HR records, this condition filters employees who conclude their projects beyond the specified due date.
- Tardiness: Derived from payroll records, tardiness is identified by pinpointing employees who start work later than 9:00 AM (hardcoded).
Each condition, whether alone or in combination, is assigned distinct risk scores to contribute to an overall assessment of an employee's time management capabilities.
Cyberloafing
"Cyberloafing" refers to the practice of using internet access for personal activities while on the clock during working hours. To identify employees engaged in cyberloafing, the pattern involves filtering UAM records. Specifically, the criteria for flagging such behavior include filtering out employees who visit external websites for more than 45 minutes on three separate occasions.
Use of Anonymizers
The Use of Anonymizers pattern relies on UAM records. This involves the application of lexicons to filter out employees who use extensions like Tor, Freegate, Zenmate, and similar tools designed for anonymizing online activities. This helps to identify instances where employees may be attempting to conceal their online presence or activities.
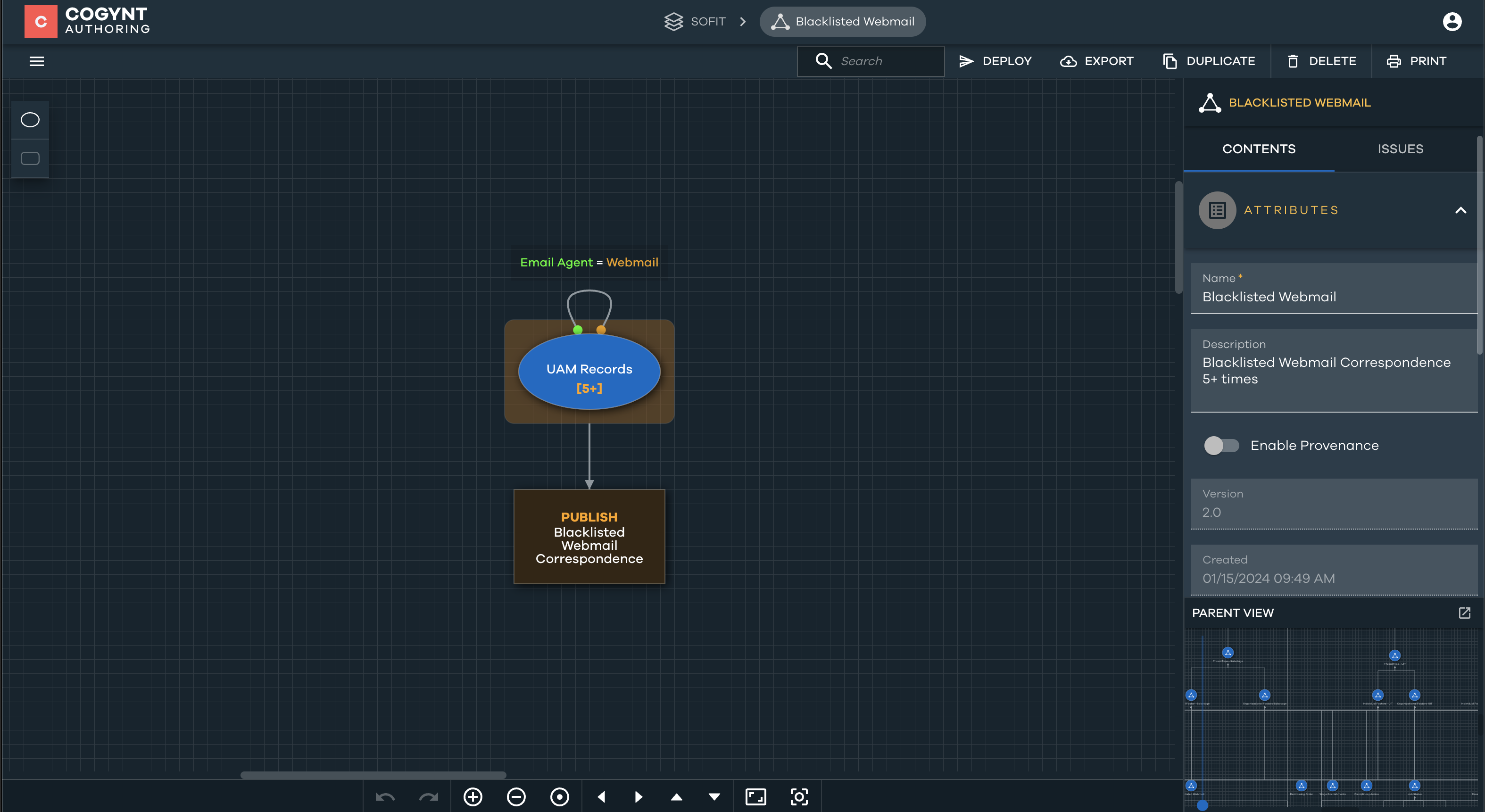
Blacklisted Webmail
The Blacklisted Webmail pattern is derived from UAM records. It involves the identification of employees who use webmail services as their email agent. This is significant, as webmail is considered less secure and more susceptible to hacking.
Restraining Order
The Restraining Order pattern is derived from the background check section of HR records. By utilizing lexicons, this pattern identifies employees who have a restraining order in place against them.
Wage Garnishment
The Wage Garnishment pattern filters payroll records to pinpoint employees who have wage garnishments.
Disciplinary Action
The Disciplinary Action pattern is extracted from HR records, and its identification involves lexicons. This pattern is designed to recognize employees who have been subjected to disciplinary action, providing insights into instances where corrective measures have been taken due to various work-related issues or violations.
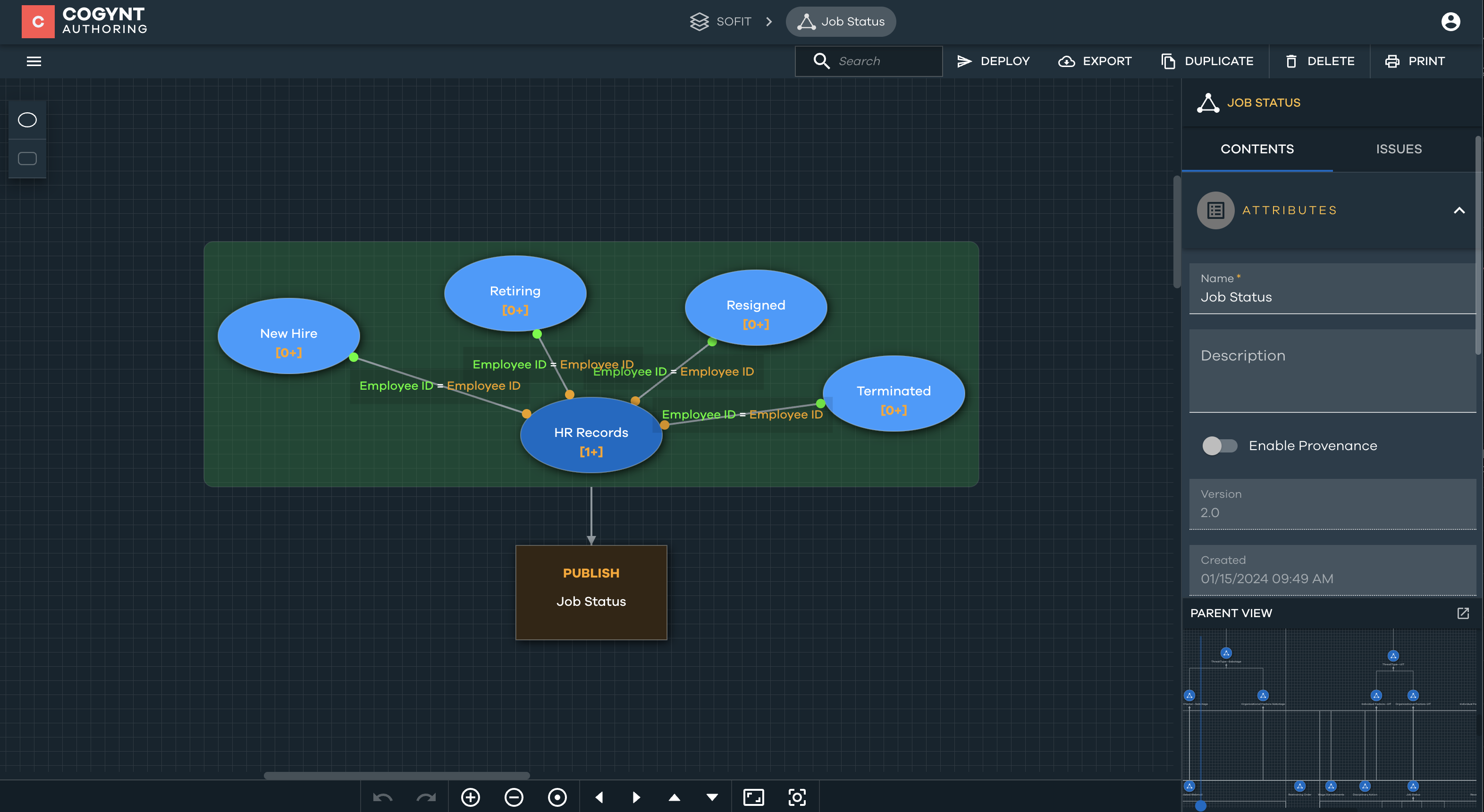
Job Status
While job status is not originally one of the SOFIT indicators, we introduced this composite pattern to maintain the model's concision. Job Status consolidates four underlying categories of SOFIT indicators:
- New Hire: Identifies employees who have been hired within the past 90 days.
- Retiring: Identifies employees in the process of retiring.
- Resigned: Filters HR records to identify employees who have voluntarily resigned.
- Terminated: Identifies instances where employees have been terminated.
The Job Status pattern examines HR records to determine whether an employee falls into one of the four categories. The pattern then assigns risk scores based on the specific condition that is met, providing an overall assessment of an employee's risk level associated with their job status.
Organizational Factors
Our model analyzes many individual factors, including the following.
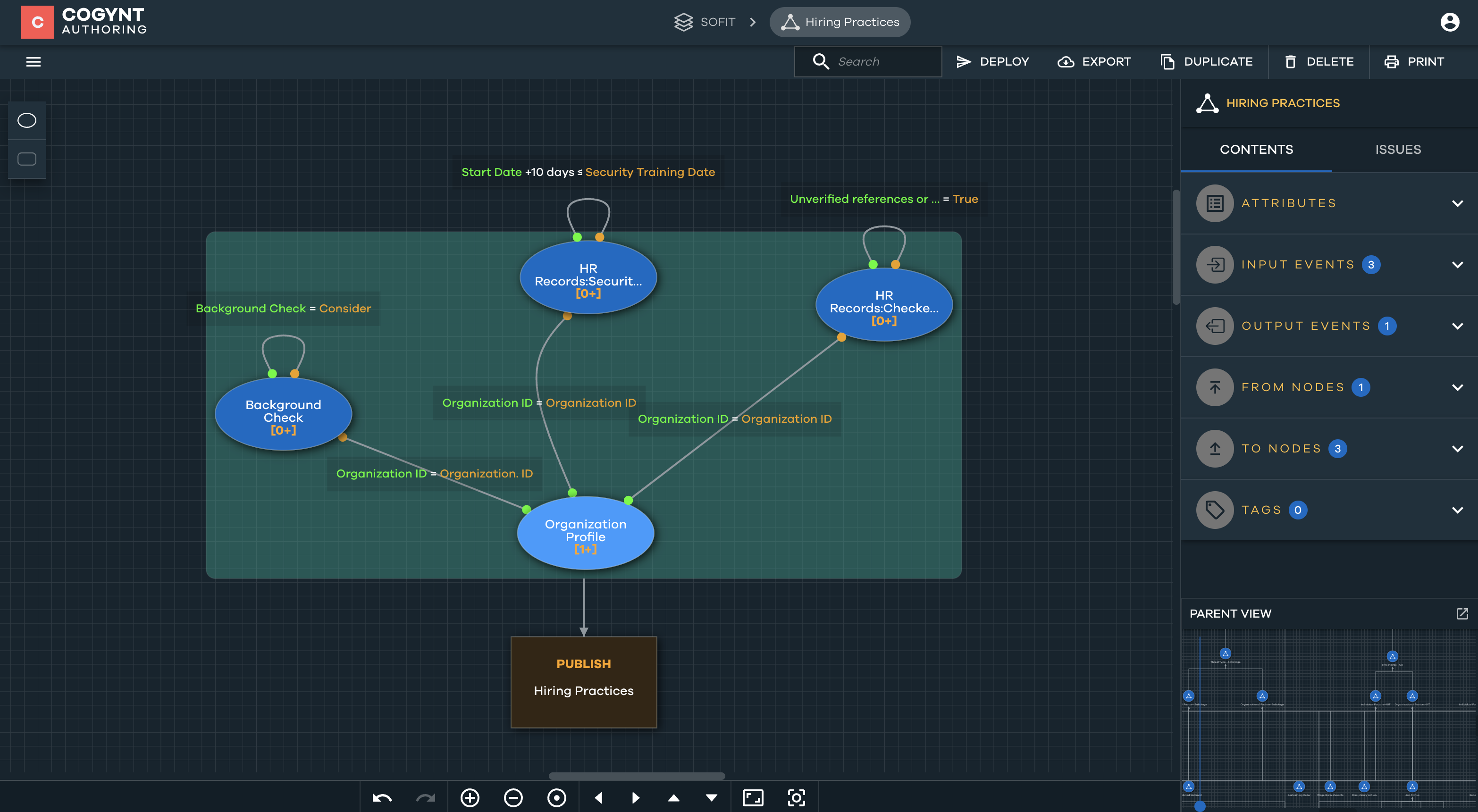
Hiring Practices
The Hiring Practices pattern assesses three distinct conditions derived from HR records:
- The first condition evaluates whether the employee's background check result was Consider instead of Clear, indicating potential concerns revealed during the background check process.
- The second condition checks whether the employee has not completed the mandatory security training within 10 days of starting the job.
- The third condition examines whether the employee's references or past employment were not verified, raising potential issues related to the verification process.
Risk scores are assigned based on different combinations of these three conditions.
Inadequate Procedures
The Inadequate Procedures pattern utilizes UAM records to identify organizations with potential deficiencies in their procedures, particularly stemming from outdated software and hardware. This pattern identifies instances where an organization has 15 or more such instances, considering a threshold of 10 years for hardware and 2 years for software. This helps highlight situations where outdated technology may contribute to operational challenges and potential insider threats.
Lack of Breaks
The Lack of Breaks pattern utilizes payroll records to identify organizations with potential issues related to employee breaks or lunches. The threshold for consideration is set at 30 or more cases, drawing attention to situations where employees may not be taking scheduled breaks/lunches as required. This can indicate organizational challenges related to work-life balance or workload management.
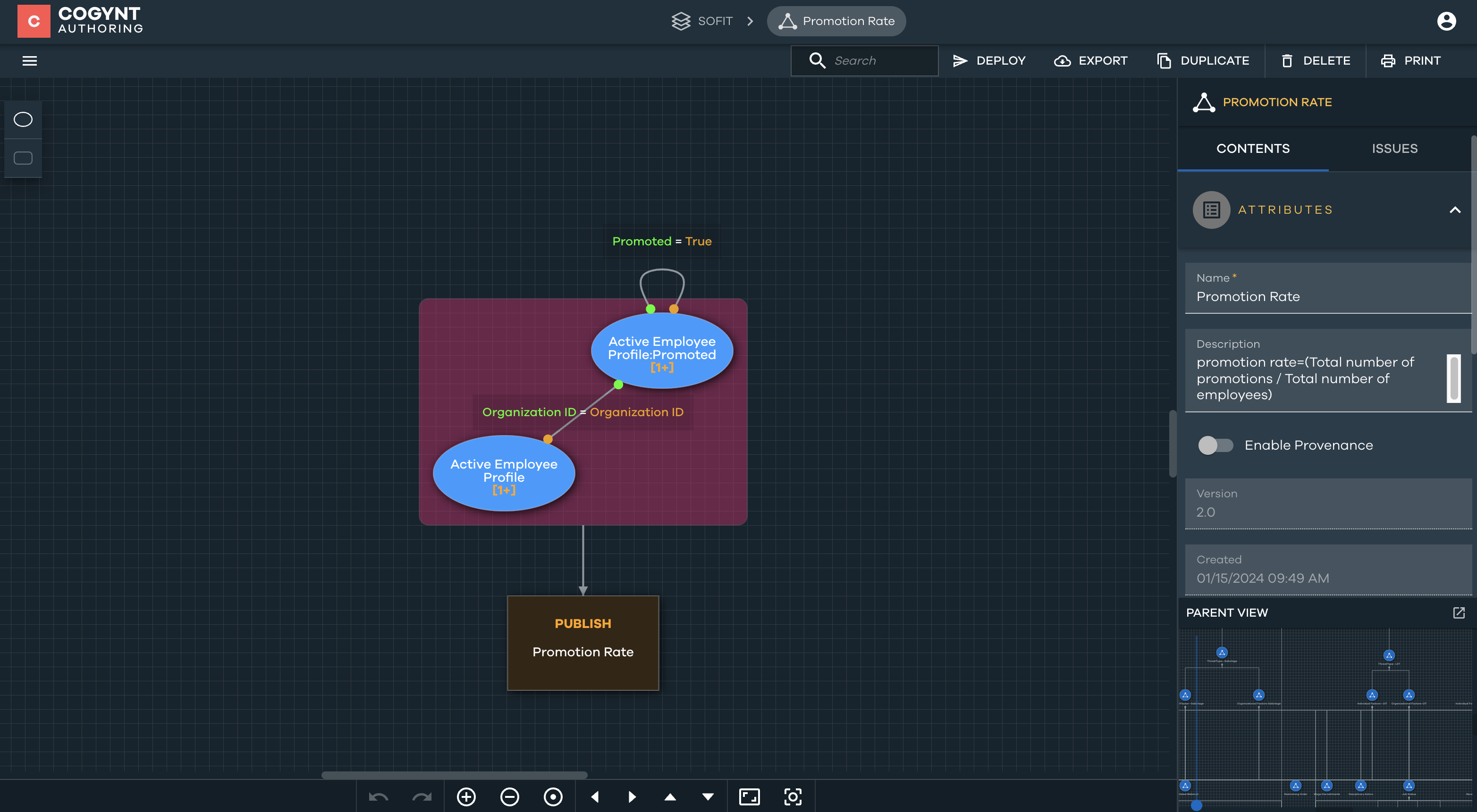
Lack of Career Advancement
The Lack of Career Advancement pattern is designed to identify organizations that may face challenges in promoting employees from within. The pattern involves calculating the promotion rate using HR records. The outcome is then filtered based on a predefined threshold, set at 0.06 (6%). Organizations not exceeding this threshold may be flagged as experiencing a lack of career advancement.
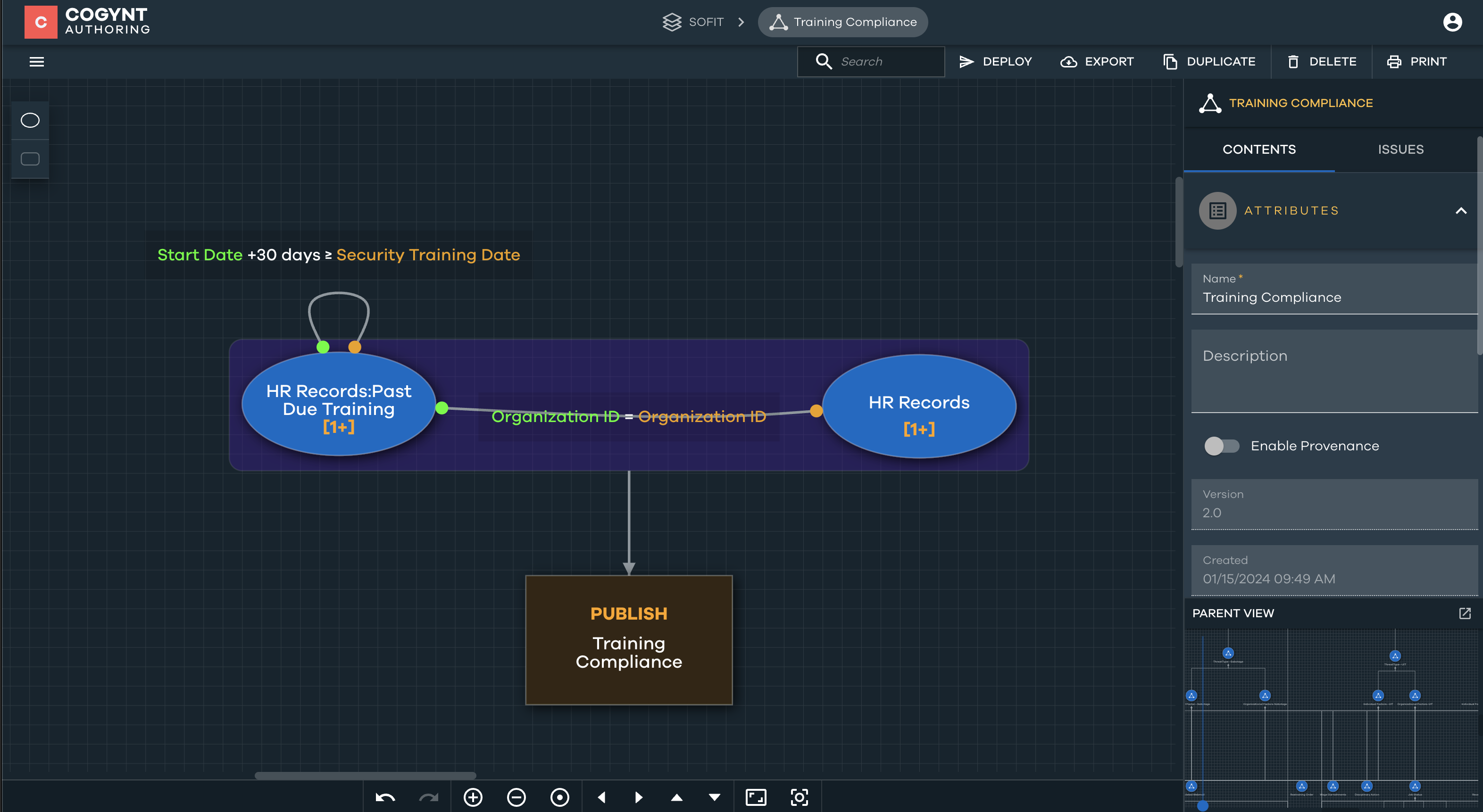
Security Training Practices
The Security Training Practices pattern focuses on identifying organizations with potential issues related to security training compliance. The calculation involves assessing the ratio of employees who have completed their security training within 30 days of their starting date. The predefined threshold for compliance is set at 95%. Organizations falling below this threshold are flagged, indicating potential difficulties with ensuring timely and comprehensive security training for their employees.
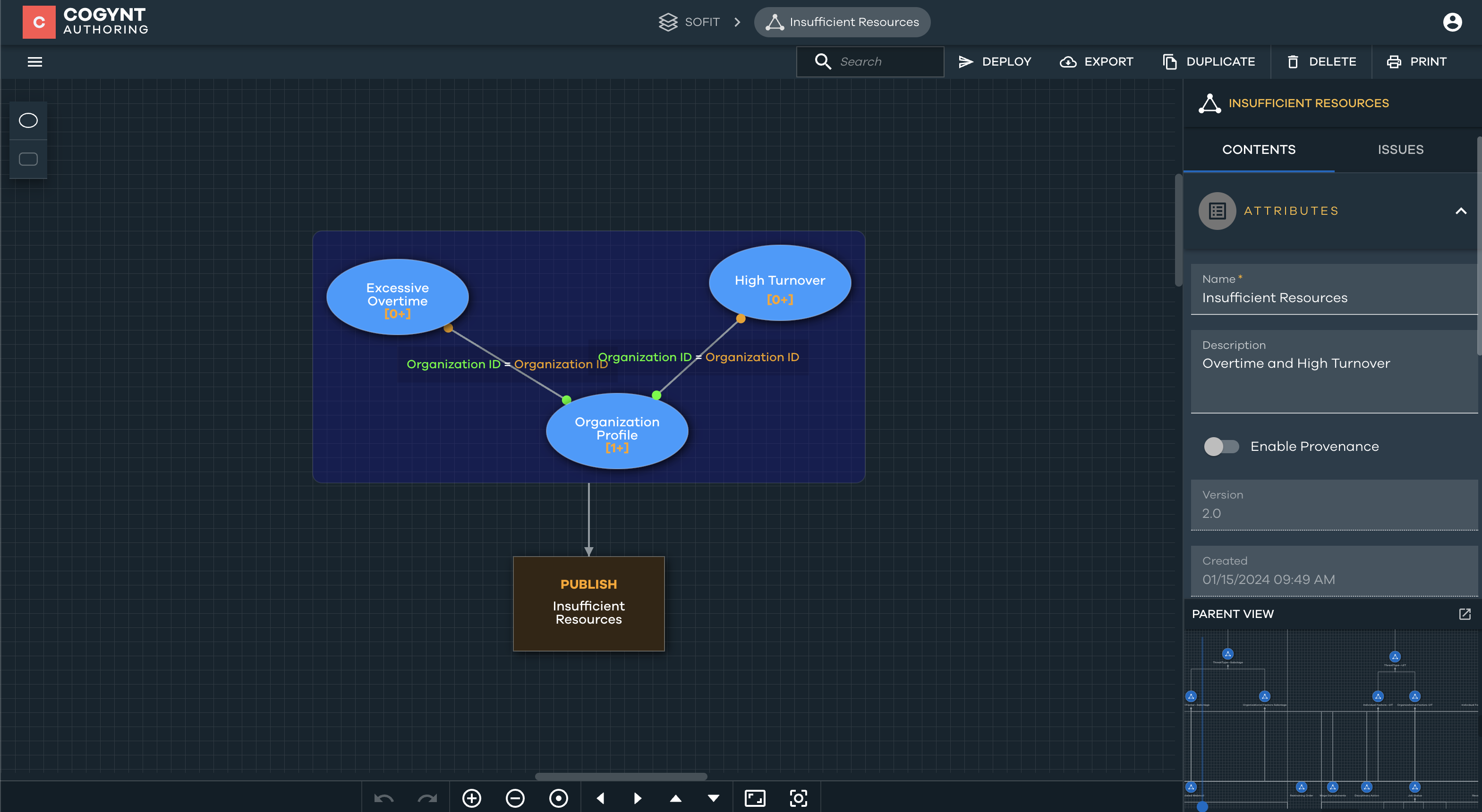
Insufficient Resources
The Insufficient Resources pattern incorporates two underlying patterns aimed at assessing potential resource challenges within organizations:
- High Turnover: Calculated using HR records, this pattern determines the level of turnover within an organization. A predefined threshold of 0.05 (5%) is applied to identify organizations experiencing high employee turnover.
- Excessive Overtime: This pattern identifies organizations with potential resource constraints by flagging those with 10 or more instances of employees working overtime for more than 25 minutes.
If either of these conditions is met, the organization is considered to have insufficient resources.
Threat Type Assessments
Cogynt uses specific combinations of threat factors to calculate the likelihood of certain threats. By evaluating the identified factors and the interplay between them, Cogynt calculates risk levels for each threat type.
Fraud
The Fraud pattern calculates the risk that somebody is undertaking fraudulent activities within an organization, exploiting their position to use the organization's information, assets, systems, or other resources for their unapproved purposes.
Sabotage
The Sabotage pattern calculates the risk that somebody is deliberately impeding organizational objectives, disrupting operations, or destroying assets.
Espionage
The Espionage pattern calculates the risk that somebody is funneling sensitive information to a foreign adversary.
Data Exfiltration
The Data Exfiltration pattern calculates the risk that somebody is stealing sensitive information.
Unintentional Insider Threat
The Unintentional Insider Threat pattern calculates the risk that somebody inadvertently poses an exploitable weakness for bad actors (for example, by using inadequate security practices).
Workplace Violence
The Workplace Violence pattern calculates the risk of somebody inflicting physical harm upon their coworkers or themselves.
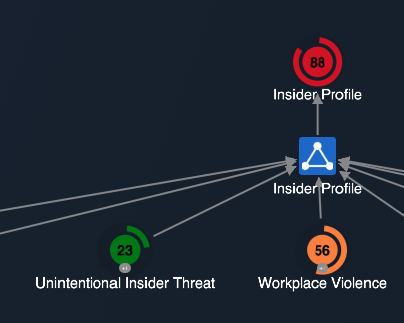
Insider Profiling
Once it has calculated and weighted all threat types, Cogynt partitions the threat types by employee number. This allows it to identify employees that pose insider threats.
The model identifies the most probable threat that each employee poses, and provides a comprehensive profile of all the indicators that led to its assessment. This intel can give organizations the opportunity to intervene and address the contributing factors before they lead to serious problems.
Doing More with SOFIT
The SOFIT model described here represents only a fraction of what SOFIT and Cogynt can accomplish. Cogynt models can include additional individual and organizational risk factors from the SOFIT knowledge base, and every factor can be fine-tuned to fulfill an organization's specific requirements.
Contact Cogility today to start mitigating your own insider threat risk with the power of Cogynt and SOFIT.